MPS falls victim to ransomware attack; sensitive information threatened to be released unless $1 million ransom is paid
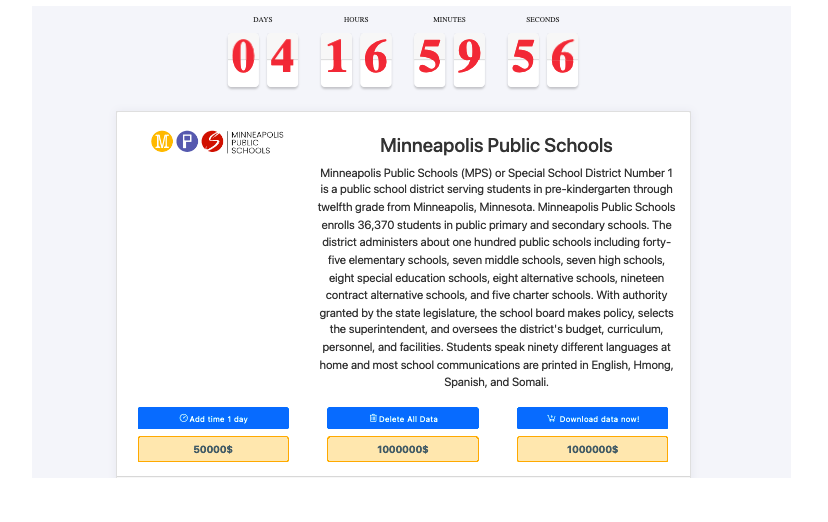
The ransomware gang “Medusa” is threatening to release sensitive files taken from MPS unless their ransom is paid by March 17th. These files potentially put thousands of current and former students, families, and staff at risk of identity theft, fraud, or worse. This screenshot, taken from the Medusa Blog, shows an active timer counting down the time until Medusa threatens to release the stolen information.
March 12, 2023
A $1 million ransom has been placed on the personal data recently stolen from Minneapolis Public Schools by the ransomware group Medusa. Unless MPS agrees to pay the ransom to the group, Medusa is threatening to release the sensitive information onto their dark web blog on March 17, giving MPS an ultimatum. Medusa also appears to offer an option to download the alleged files for the same price or extend the deadline for a $50,000 fine. If the files were to be downloaded or exposed it could jeopardize the personal information of thousands of current and former students, families, and staff including financial information, home addresses, and Social Security information. Morgan Fierst, a South math teacher, noted that as of March 10, teachers have not received any additional information about the situation, aside from the general notices sent to the public.
To prove they successfully accessed MPS data, Medusa published a 51-minute-long video showing some of the files that were stolen. The district was able to remove the video within several hours of it being posted, but the data contains information dating back as early as 1995.
What MPS has been slightly misleading about, however, is that the contents of the video were also published to Medusa’s site on the dark web. This means that it is anonymous and nearly impossible to remove, even with the assistance of law enforcement. Leaked data includes personal phone numbers, home addresses, and personal email addresses of staff, students, and parents, teacher employment information and salaries, grant information, contracts, names of student sexual assault victims, school bank account deposit records, student IDs including photos, and more. Only a small fraction of the data in Medusa’s possession has been published so far, but what was already exposed has the potential to cause major damage.
Lydia Huff, a senior at South, feels that students shouldn’t have to be worried about this kind of issue. “As students, we should be focused on school and stuff like that, not on whether our Social Security information is going to be leaked.”
On Tuesday March 7, over 2 weeks after initially revealing some sort of encryption event had occurred, MPS announced that “The threat actor who has claimed responsibility for MPS’s recent encryption event has apparently posted online some of the data they accessed from MPS.” The district added that it had alerted law enforcement, was contacting impacted individuals, and was working with the “online host company” to remove the information as soon as possible. It is unclear if any potential victims have been contacted at this point.
MPS currently has a page on its website regarding new information on its investigation into the ongoing situation. The latest update, posted Thursday March 9, states, “While our investigation and system restoration is ongoing, MPS has not found any evidence that any data accessed has been used to commit fraud.” It also added that it was working with 3rd party forensic IT specialists to monitor MPS systems via “advanced endpoint detection and response tools, including Carbon Black.” VMware Carbon Black is a cybersecurity tool that utilizes endpoint detection and response tools which are designed to detect unusual activity on an organization’s devices or networks and block malicious files from attackers.
Fierst spoke about what she hopes MPS will do moving forward. “I wish they would choose the least amount of destruction to the students, families, and staff in our district. I feel like they don’t care about us as people, I think that was made very clear last year. I wish they would make a choice that was in the best interest of the students and families they are serving.”
MPS first announced that it had experienced what it referred to as an “encryption event” as early as February 21. This attack affected many MPS systems that are necessary for the school day, such as Gradebook, Student Portal, school internet, phones, cameras, badge access, copiers/printers, building alarms, and more. Initially, parent-teacher conferences were canceled and in an email to staff, students, and parents, MPS announced it was “experiencing technical difficulties with some systems.” The only information given was that the technology required for e-learning was still accessible, as the district was in the midst of 3 e-learning days.
The district’s IT department sent out more information around 4 hours later on the same day. In the vague email, MPS stated that “Staff [were] working around the clock with third-party (non-MPS) IT specialists to investigate the source of this disruption, confirm its impact on our systems, and restore full functionality to everyone as soon as possible.” It was added that “viable backups” were used to restore “impacted data” and prevent data loss.
Over the following weekend, all teachers and students were locked out of their accounts and devices as the IT department changed all passwords. It was originally announced that all staff and students would have received their new logins by Monday February 27, distributed individually via paper. Most staff were able to regain access to their accounts by the end of the day, but students were not.
The process of distributing new student logins began on Tuesday February 28 and continued throughout the week. Because some students still did not have access to their accounts and devices, classrooms could not function properly.
After staff and students regained access to their accounts, everything started to feel back to normal. MPS did release some limited additional information, announcing that the attackers “May have been able to access certain data located within the MPS environment.” It also warned of “suspicious emails or phone calls” and encouraged staff to change passwords for personal accounts accessed on MPS devices, monitor financial accounts, and check and freeze their credit reports. However, MPS stated that these measures were “a best practice and out of an abundance of caution,” downplaying the significance of the data breach and removing a sense of urgency. All of MPS’s communication regarding this so-called “encryption event” have been very vague and cryptic, failing to warn the community of the significance of the attack.
Hawke added that she believes the lack of clear communications has led to further confusion and chaos, and that the messages that have been sent have felt “very vague.”
This ransomware attack on MPS isn’t an isolated event; the Medusa website features dozens of other organizations that have fallen victim to their attacks. The majority of these have had the entirety of their data published after failing to pay the requested ransom money. MPS is currently faced with a difficult challenge: deciding whether or not to pay the ransom.
Now that Medusa has this data, every outcome has huge repercussions for both the victims and the district as a whole. Even if MPS does pay the ransom, there is no guarantee that Medusa won’t publish the data anyways or abuse the information in another way. The best-case scenario currently is for law enforcement to fully shut down the Medusa Team. Unfortunately, this is unlikely as Medusa has targeted many other organizations already and has been able to continue its operations.
All current and past MPS students, staff, and parents, should be taking this security threat very seriously. Fierst says that she has frozen her bank accounts and is in the process of changing all of her passwords. “I just did the simple things that I could do with the time that I had.” She feels that these small things are worth doing now if there’s any chance they could help in the future. To keep yourself safe, change your passwords for all websites you may have accessed on an MPS device and enable multi-factor authentication when it’s available. Make sure all of your passwords are secure and not used for more than one site. Monitor your financial accounts, put freezes on credit scores, and be careful of fraudulent emails, phone calls, and texts.







Lasai • Mar 13, 2023 at 10:01 am
Wow this is super informing thanks!